The password. From “Open sesame” to “P@ssw0rd1”, the password is almost as widespread as the internet. They are used for everything from unlocking your iPhone and paying your taxes to logging onto your STEAM account or playing some Minecraft.
Large companies, however, are trying to move away from passwords. Tech giants like Microsoft, Google, Apple, and many others are slowly trying to kill the password and build up more secure alternatives. Why are these companies so anti-password? Why are they trying fundamentally to change the way we access our online accounts?
Here, I’d like to discuss some of the reasons passwords are insecure and why companies are trying to replace them.
Password Reuse
The first problem with passwords is password reuse. Often, people use the exact same password for multiple accounts across different websites. While this might be fine in a perfect world, if a user is tricked into entering their password into the wrong website or if a data breach happens, all accounts across all websites sharing that password are as good as hacked.
In theory, users should have a different password for every website. This way, even if one password gets leaked, the rest of the user’s accounts are secure. We see, however, that this doesn’t work in practice. Many studies have shown that users reuse their passwords all across the internet without changing them. In addition, if a person did have unique passwords for every single website, how are they supposed to remember all 500+ passwords spread across the internet? This leads to the next problem…
Weak Passwords
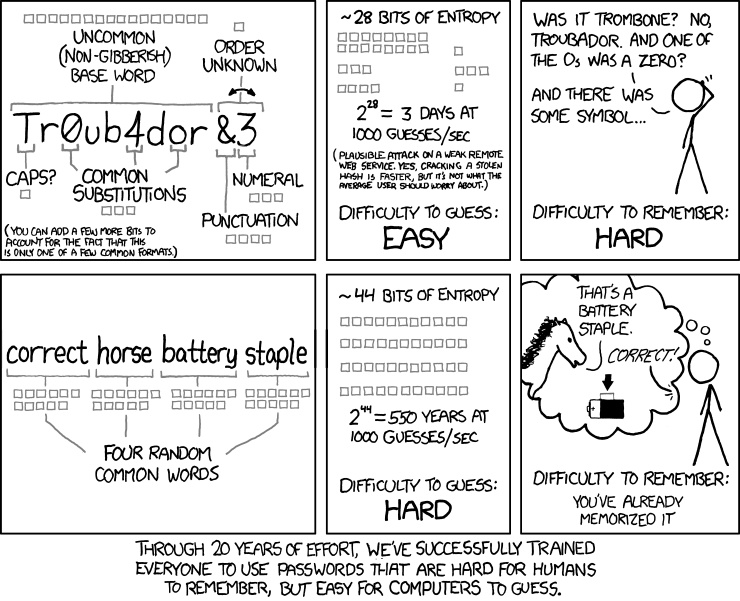
When people are forced to use so many different passwords, they often use passwords that are easy to remember. The problem is that these passwords are usually easy to guess. One survey run by Google and The Harris Poll found that 24% of people have used “abc123”, “password”, “123456”, “Iloveyou”, “111111”, “qwerty”, “admin”, “welcome”, or some variation thereof in their passwords, making them much easier for a hacker to guess. In addition, 59% of those surveyed said that they had incorporated some name or important date into their password. This means that, with a little research, a hacker could significantly narrow down the range of passwords they have to guess in order to access someone’s account. Finally, out of the 27% of the people who had tried to guess another’s password, with almost 20% of them successfully guessed the password. This just further reinforces that with a little research, hackers could probably guess a majority of users’ passwords.
In addition, hackers often use lists of breached and common passwords to attempt to access users’ accounts. One list, Rockyou.txt, contains over 14 million passwords which hackers will guess over and over until eventually they find a match. These passwords have all been in use at one period or another, so hackers figure that if someone has used that password once, they are likely to use that password again on another website, whether that be their Spotify or their bank account.
To summarize, the problem is that memorizing unique, hard-to-guess passwords can be extremely hard, especially if you’re using a different password for each of your accounts. As a result, users make their passwords easy to remember and thus easy to guess.
Forcing People to Change their Passwords Doesn’t Work
One solution proposed to counter some of these problems is forced password changes. This is a widely debated topic in the cybersecurity industry right now (here’s one small discussion), but this policy forces people to change their password every 90 days or so.
On one hand, forcing users to change their password helps negate some of the effects of data breaches. If someone’s password is breached, then the leaked password will become useless 90 or so days after it was created.
On the other hand, if you have to keep changing your password, you’re more likely to use easy-to-guess passwords or just make simple changes to your previous password (like adding a 1 to the end of it). In addition, forcing password changes encourages users to write down their passwords so that they remember them more easily. Microsoft no longer recommends mandated password changes, and NIST (the US government body which gives companies cybersecurity advice) says that companies shouldn’t force users to change their passwords periodically. Again, this topic is still very much in contention, but it seems that forcing users to change their passwords doesn’t solve the disadvantages of passwords in general.
The Conclusion
This is why the password is slowly dying. Companies like Apple, Google, Microsoft, and others are working with organizations like FIDO to try to end the need for passwords across the web.
Until they complete their goal, enabling 2 factor authentication (2fa) for signing in is one of the best ways users can protect their accounts. Rather than just verifying that the user knows a piece of information, 2fa also either verifies that the user has some device on them (an authenticator app) or determines the user’s identity in some other way (like biometrics). Some of these methods are better than others (for example, verifying a user’s identity by texting them is insecure and biometrics should never be synced to the cloud), but using a secure 2fa method like an authenticator app will dramatically increase your account security. Even an insecure method of 2fa is better than no method at all!
Another method users can use to protect their accounts is using a password manager. A password manager stores all of a user’s passwords so that they don’t have to memorize them. This means that a user can have a different, hard-to-guess password on each site without the need to remember 50 million passwords. Password managers built into browsers by default are good, but it’s usually better to use a password manager which isn’t included in the browser by default. My current choice is Bitwarden, and I’ve written a separate blog post about why I chose them. Password managers aren’t as good as 2fa – hackers can still try to guess user’s passwords – but it’s much better than doing nothing at all. In addition, combining this with 2fa is probably the best, easiest method most users can take to secure their online accounts.
While a passwordless future may be five to ten years (if not more) into the future, hopefully the password will soon be a relic of a bygone day, relegated to the same place in history as CD ROMs and floppy disks. As long as a suitable replacement can be found, it should be clear now why passwords should be eventually removed from the digital ecosystem.
Sources:
- I was inspired to write this blog post after listening to an episode of The WAN Show where Luke and Linus discuss password managers.
- CISA’s list of bad practices
- Thanks to krypticbit for the title of this post